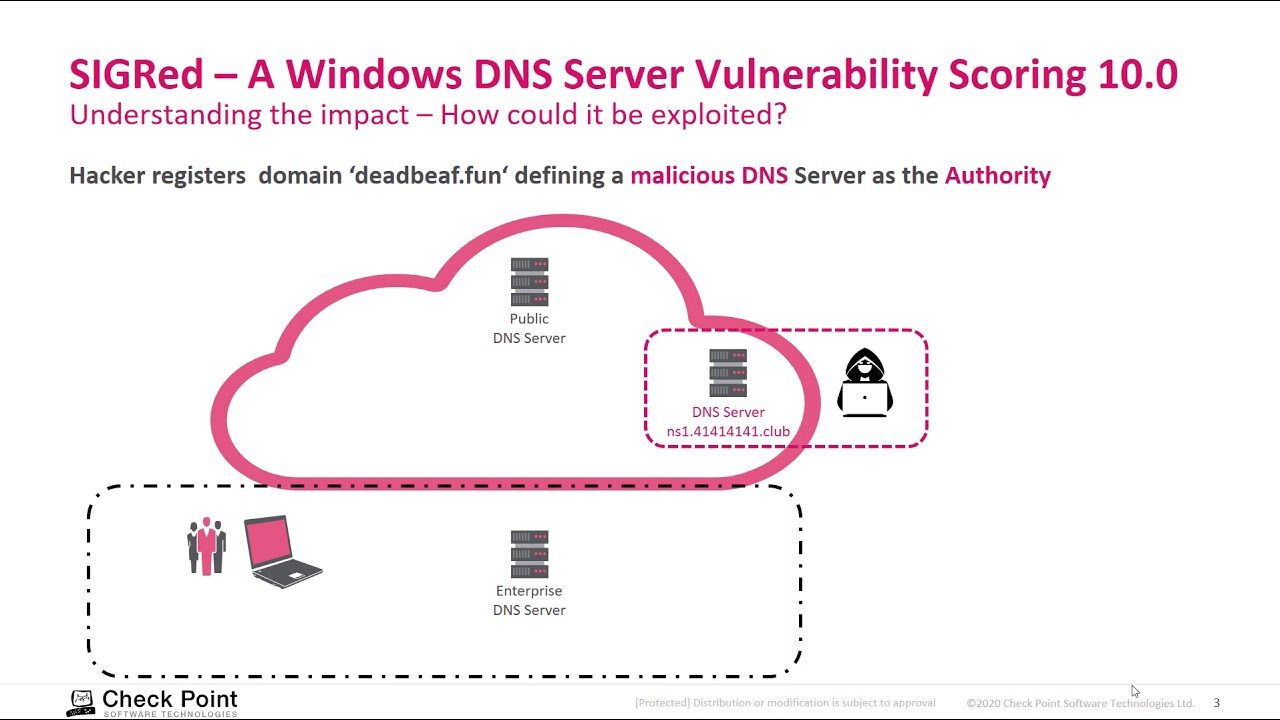
A wormable remote code execution
The vulnerability, tracked as CVE-2020-1350, was discovered by researchers from Check Point Software Technologies, who dubbed it SIGRed, a play on the vulnerable function name that handles DNS SIG queries. The flaw received the maximum CVSS severity score of 10, making it critical, and according to Microsoft, it's wormable.
"Wormable vulnerabilities have the potential to spread via malware between vulnerable computers without user interaction," the Microsoft security team said in a blog post. "Windows DNS Server is a core networking component. While this vulnerability is not currently known to be used in active attacks, it is essential that customers apply Windows updates to address this vulnerability as soon as possible."
It's worth noting that this vulnerability does not affect the Windows DNS client component that is used to query DNS servers, but the server component which answers DNS queries. Because of this the flaw affects all versions of Windows Server starting with 2008 that have the DNS role installed but does not affect the desktop versions of Windows.
Not all Windows servers are configured to act as DNS servers, but Windows domain controllers usually do, and they sit at the core of Windows networks. An attacker who successfully exploits the SIGRed vulnerability can run arbitrary code in the context of the LocalSystem Account, giving them full control over the affected system. If those systems are domain controllers, the impact extends to the whole network.
Mitigations for SIGRed
Organizations are advised to install the security patch released by Microsoft as soon as possible. If they can't update their systems immediately, they can apply a registry workaround manually.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters
DWORD = TcpReceivePacketSize
Value = 0xFF00
The DNS service needs to be restarted after this registry modification for it to take effect.
About the author |
|
 |
Tom Thorp is an IT Consultant living in Miami on Queensland's Gold Coast. With more than 30 years working in the IT industry, he has extensive experience. The IT services provided to clients include:
Website development and hosting,
Database Administration, Server Administration (Windows, Linux, Apple), PBX Hosting and Administration, Helpdesk Support (end-user & technical). |
| If you like any of my content, consider a donation via Crypto by clicking on one of the payment methods:. | |




