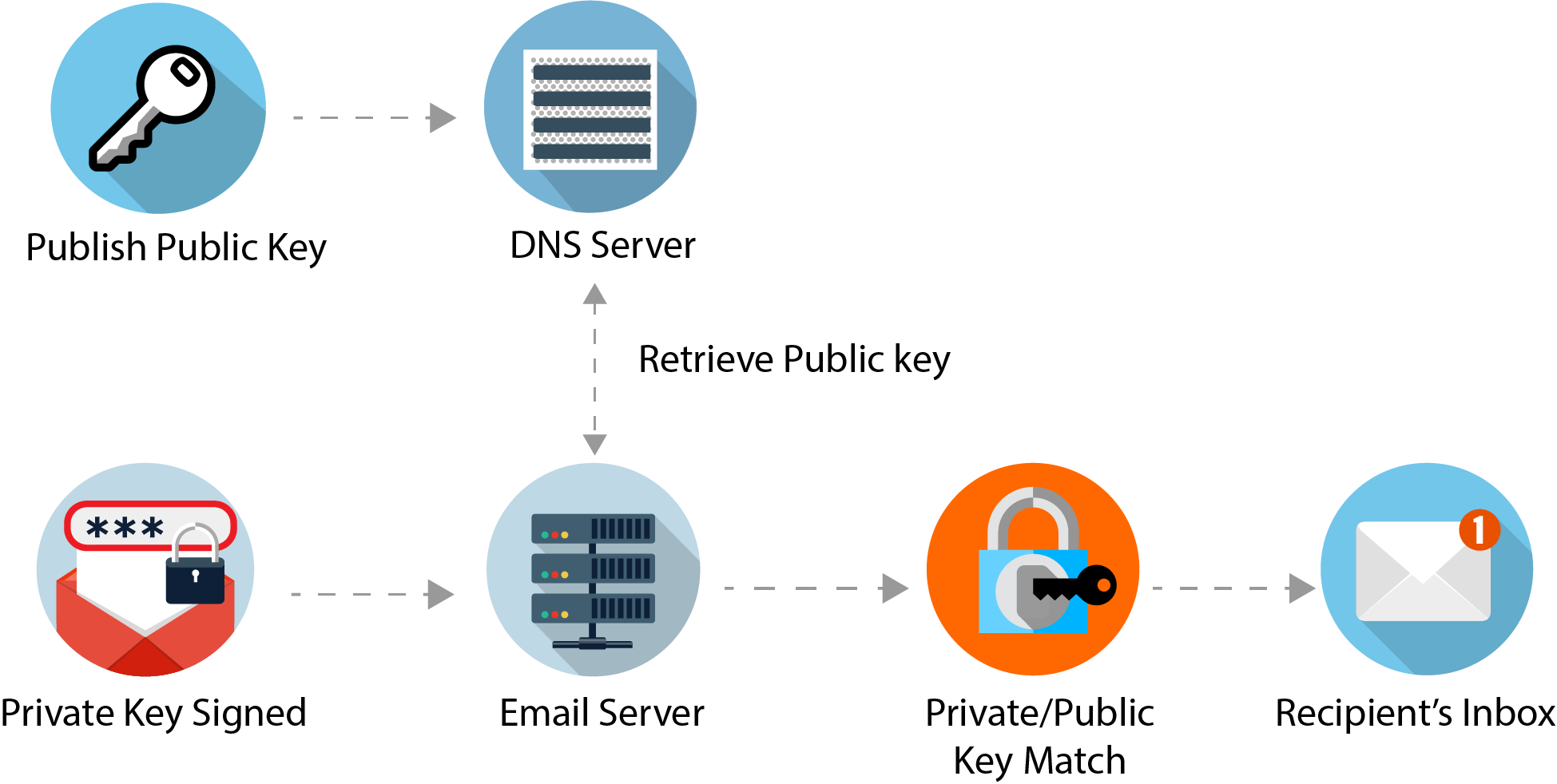
What is DKIM?
DKIM (DomainKeys Identified Mail) is a service that allows outgoing emails from your email server to be signed via the email message headers. The DKIM message header uses the public key of your domain, and is a check for destination email servers to verify against, that your email is genuine and has not been altered in transit.
DKIM's Role
The main role DKIM plays, allows the destination email server to securely verify incoming emails from a sending domain's MTA (Message Transfer Agent). This is done by comparing the hash value created by the MTA in the message header of the email, with the public key associated with the MTA's domain. The recipient MTA then uses that key to decrypt the hash value in the email’s header and simultaneously recalculates the hash value for the email message it received. If both keys match, then the email has not been altered in any way.
Installing DKIM
To install DKIM on Fedora, execute the following commands.
dnf install opendkim
Configuring DKIM
Setting up DKIM is dependent on your MTA. In my setup, I am using Postfix as my preferred MTA.
Within Postfix, make sure that the 'milter port number' matches to the Socket assigned to OpenDKIM. Thus :
/etc/postfix/main.cf
============
.
.
milter_default_action = accept
milter_protocol = 2
smtpd_milters = inet:localhost:8891
non_smtpd_milters = inet:localhost:8891
/etc/opendkim.conf
============
.
.
Socket inet:8891@localhost
To create your DKIM keys for your MTA, issue the following commands :
$ MYDOMAIN=<your domain>
$ mkdir -p /etc/opendkim/keys
$ cd /etc/opendkim/keys
$ opendkim-genkey -t -s <your selector> -d $MYDOMAIN
then rename your private and txt files thus :
$ mv <your selector>.private <your selector>.<your domain>.private
$ mv <your selector>.txt <your selector>.<your domain>.txt
finally, protect your private keys :
$ chmod 600 *.private
Finally, we have to insert the public key as a TXT entry in the Zone file of our MTA's domain. To do so, we first have to copy the contents of the public key, which is contained in the OpenDKIM text file. Here is an example :
mail._domainkey.example.com IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC65tv6LhAbbrqcwgyBaC
x50scjedj357we9SJdff6VHOKDYgU/kvuV2rQiedHjtJDPuFJIwoNqh8pbIWxcZ8J2FhVhXU1QWdBmOQ/w61jfsyVAMrX/SrcJAd/1
XHYcS4o3uIOV7jICVOJLiYW5wjYLvWpPoraQzQE1Npjlsx2T5QIDAQAB" ; ----- DKIM key default for example.com
where 'mail' = your selector, and 'example.com' = your domain. However you administer your zone file, for DKIM to work it is mandatory to include the TXT record into your MTA's zone file.
Restart your services to enable the new changes.
$ systemctl restart named-chroot // if you administer your primary named server
$ systemctl restart opendkim
$ systemctl restart postfix
check the status of your services as well as your journal files for any startup errors.
To test that DKIM is reporting your MTA correctly, run the following command :
$ opendkim-testkey -d <your domain> -s <your selector> -k <path to your domain private file> -vvv
Providing your DKIM configuration is ok, the output should be similar to the following :
opendkim-testkey: using default configfile /etc/opendkim.conf
opendkim-testkey: key loaded from /etc/opendkim/keys/mail.example.com.private
opendkim-testkey: checking key 'mail._domainkey.example.com'
opendkim-testkey: key OK
Final Check
As a final check, send an email from your MTA to an email address you manage, and check the message headers. If your MTA is sending DKIM requests in the message headers correctly, the receiving MTA should pass DKIM authentication. Here is an example where I sent an email from 'tomthorp.me' to an email address on 'hotmail.com' :
Authentication-Results: spf=pass (sender IP is 139.99.219.56)
smtp.mailfrom=tomthorp.me; hotmail.com; dkim=test (signature was verified)
header.d=tomthorp.me;hotmail.com; dmarc=pass action=none
header.from=tomthorp.me;compauth=pass reason=100
Any questions on this howto, please leave in the comments section below.
About the author |
|
 |
Tom Thorp is an IT Consultant living in Miami on Queensland's Gold Coast. With more than 30 years working in the IT industry, he has extensive experience. The IT services provided to clients include:
Website development and hosting,
Database Administration, Server Administration (Windows, Linux, Apple), PBX Hosting and Administration, Helpdesk Support (end-user & technical). |
| If you like any of my content, consider a donation via Crypto by clicking on one of the payment methods:. | |




